Blog
What is Cloud Security: Challenges & Solutions
The majority of web owners are becoming familiar with the benefits of digitalization and the dangers of cyber-crimes and hacker attacks. Hence, these website owners try to secure their websites in multiple ways, out of which backing up or storing website data and information to cloud storage is one of the best security solutions. However, little do they know that hackers are also eyeing these cloud storage and are looking for cloud leaks to gain sensitive data.
Cloud Security Breach Statistics indicate that:
- 80% of the businesses have faced a cloud data breach in the last 18 months
- 43% of the businesses have reported ten breaches or more
What is a Cloud Leak?
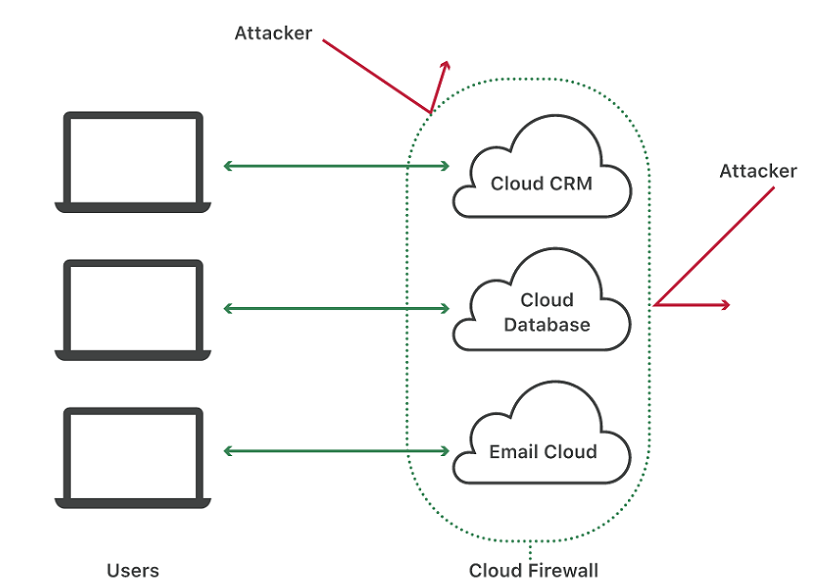
Cloud leak is accidental exposure of data stored in the private cloud on the open internet. This private storage space comprising of sensitive data is secured with a firewall. However, sometimes, the storage door may be left unguarded or open by a negligent employee, which may cause leakage of data.
This may expose cloud data causing irreparable damages to the business. In addition, vulnerabilities in the cloud server or cloud gateways unlatched on the public internet may also cause cloud leaks and data exposures.
How to secure it by preventing leakages and disasters is a challenging task. The same can be resolved by implementing cloud security solutions.
What is Cloud Security?
Cloud security is an amalgamation of various policies, multiple applications, and security solutions that secure the data stored within the cloud. The cloud security umbrella comprises five main archetypes defined by Gartner.

1. Cloud Access Security Broker (CASB):
CASBs are those security policy enforcement points located between cloud service customers and cloud service providers.
These security brokers are ideal for detecting malware and other forbidden cloud applications. They also help in tracking user behavior and conducting audits on the same.
CASBs work the best in SaaS environments.
2. Cloud Workload Protection Platform (CWPP):
This workload protection platform fulfills the cloud’s protection requirements in the cloud, which comprises applications and processes.
Since CWPPs are multi-functional, they are proficient in taking care of system hardening, taking care of system vulnerabilities, managing workloads, etc.
3. Cloud Security Posture Management (CSPM):
CSPM is a risk detection cloud solution, which detects the security loopholes in the cloud. Apart from detecting, they log and report the same. As a result, they work the most efficiently in multi-cloud IaaS environments.
4. Cloud Infrastructure Entitlement Management (CIEM):
CIEM specializes in focusing on taking care of cloud risks and access management. PaaS and IaaS environments mainly use CIEM for applying for permissions. It prevents not only liberal access but also protects personal data by enhancing appropriate visibility and access.
5. Cloud-Native Application Protection Platform (CNAPP):
CNAPPs are meant to detect and secure cloud data and other applications, including hosts, VMs, etc.
Things to Know About Cloud Security:
1. Expensive and Rising Cloud Leaks:
Cloud-based attacks rose to 630% between January 2020 – April 2020. These cloud leaks occur due to cloud misconfigurations and are proving to be more costly than other breaches.
Statistics by Accurics indicate that cloud leaks and misconfigured clouds comprise approximately 200 breaches (300 million records) exposed in 2 years.
Some major cloud breaches include Capital One, State Farm, Docker Hub, etc.
ii. Misconfiguration & Integration:
Misconfiguration and integration of cloud services by employees may invite cyber-criminals to your storage house.
Capital One is a perfect example of cloud misconfiguration.
iii. Humans Responsible for Cloud Security Problems:
Big cloud providers like Microsoft Azure, Cisco Systems, etc., have default configurations done privately. Hence an open gateway may enable an employee to interfere and switch default settings.
iv. API (Application Programming Interface) is Weak Link:
Weak spots in the cloud server may bring uninvited guests to your cloud’s doorstep. Ensure that your API is strong to prevent such intrusions.
v. A Target for Cyber-criminals:
Cyber-criminals use the same strategies like phishing, malware, brute-force attacks, etc., to enter the cloud server and steal login credentials.
vi. Ignorance About Data Exposure:
Unawareness about the data privacy being invaded in the cloud network may prove costly.
vii. Pending Updates:
The cloud server may succumb to hacker attacks in the absence of security updates. This cloud computing vulnerability can affect both the cloud provider as well as the cloud user.
Cloud Security Challenges:
Anything which is publicly shared comes with its share of risk. Be it public Wi-Fi or public cloud, ensuring their security is always a challenge for cloud providers and cloud users.
Below-mentioned is a briefing on the cloud security challenges which need to be taken care of before they cause catastrophes.
i. Increased Attacks:
Public cloud services are becoming extremely popular due to their low costs, maintenance-free technology, and unlimited scalability.
Hence hackers eye these clouds and exploit poorly configured clouds to gain access to the cloud storage. They create havoc by installing malware or other malicious codes and links to gain access.
ii. Absence of Visibility and Identification:
Though cloud providers are in complete control of their cloud infrastructure, they are kept exempt from customers for security issues.
This applies to all the cloud models, i.e., IaaS, PaaS, and Saas. Thus cloud visibility, data tracking, and identification of cloud assets are missing.
iii. Workload Change is Phenomenal:
Changing workloads in cloud storage are constant due to the rise in growth or the dip in utilization. This lessens the security strength since security tools are ineffective in protecting the information in flexible environments.
iv. Unwanted Privileges:
Many times cloud providers grant immense privileges to cloud users, irrespective of their requirements.
Example: Rights for deletion or modification of the database.
Untrained employees can leave cloud leaks while accessing the data, which paves the way for hackers.
v. Improper Key Configurations:
Even the employees who use the cloud on an application-level need to properly configure the keys to ensure that the storage is not exposed to risks.
vi. Management Complexity:
Managing cloud complexities is a tough call since security needs to be maintained on all cloud platforms, i.e., public clouds, private clouds, etc.
v. Difficulty in Maintaining Cloud Compliance:
Though the cloud providers are compliant with the government rules, cloud users should also ensure data compliance. Unfortunately, this becomes a challenging task since poor visibility and lack of access make the compliance task difficult.
Cloud Security Solutions:
Cloud servers located in private internet warehouses are inaccessible and have encrypted data, making it difficult for hackers to access or misuse.
Still, your cloud server needs ample security to stay safe from these intruders.
Let me brief you about some of the cloud security solutions used by cloud providers for storage security.
i. Regular Security Updates:
You often click “later on” on the update notifications, which is a risky move. These updates patch up your security lapses and keep your digital infrastructure secured from cyber thieves.
Your cloud server also needs regular security updates, which your cloud service providers need to take care of.
ii. Data Encryption:
Opt for those cloud service providers that use encryption security to secure your data. For this, you need to use an SSL (Secure Socket Layer) certificate for cloud data security. This move will sway hackers away and keep your data safe since hackers don’t appreciate scrambled data.
Example: Comodo Wildcard SSL can help in securing the chosen main domain and an unlimited number of first-level subdomains at an affordable price.
iii. Benefits of Comodo Wildcard SSL:
- Quick Issuance
- Multiple subdomains are secured.
- 256-bit Encryption with 2048-bit CSR encryption
- 99% Browser-server compatibility
- Unlimited Server Licenses and SSL re-issuances
- Warranties and Money-back Guarantee
iv. AI for Security:
Nowadays, cloud providers resort to Artificial Intelligence (AI) for their server and data security. AI has inbuilt algorithms which help detect security lapses in the security systems.

v. Inbuilt Firewalls:
Cloud servers have inbuilt firewalls to protect your data storage. These firewalls act as a shield and keep malicious traffic away from accessing your data. Hence hackers find it strenuous to insert malware via these securities set by the cloud service provider.
Cloud servers have inbuilt firewalls to protect your data storage. These firewalls act as a shield and keep malicious traffic away from accessing your data. Hence hackers find it strenuous to insert malware via these securities set by the cloud service provider.
vi. Redundancy:
Your cloud providers may also face emergencies like hardware failure or server crashes. But, most cloud service providers make multiple backups of your data to varied locations (data centers) or servers.
This redundancy helps them in case of unwanted contingencies.
vi. Third-Party Security Testing:
Cloud providers should also use another security company for testing their servers. This move also strengthens their security and keeps cyber-criminals away.
Few More Cloud Security Solutions:
Businesses that resort to cloud security solutions should ensure:
Cloud data visibility, data accessibility, and data control for tightening the security ropes around the cloud servers.
- Visibility is possible by gaining complete access to data via an API connection, like which users can access data, location of data, source of data download, etc.
- Post visibility, controls can be put on the data, such as preventing sensitive data from leaving the cloud server, protecting intruder entry, disable access in case of suspicious activity, etc.
- Cloud data accessibility is vital, and hence controls should be given to authorized personnel only. In addition, identifying malicious behavior, preventing malware, and other access control techniques should be implemented for data safety.
Conclusion:
Constant monitoring is a pivotal part of cloud security solutions. This helps to fix the cloud leaks before a cyber-attack. With almost 70% of the companies using cloud services, it’s essential to confirm your cloud provider’s security solutions and how they face the cloud server challenges for securing the cloud data.
Global SSL service providers like SSL2BUY help in encrypting the cloud data, so check out whether your cloud service provider uses the same for ensuring data privacy or not.

 Blog2 years ago
Blog2 years ago8 Best Bulk and Mass Emails Software for Email Blast

 Blog2 years ago
Blog2 years ago50 Highest Paying Affiliate Programs to Earn Crazy Commission in 2023

 Blog2 years ago
Blog2 years agoWhat is Guest Blogging? And Why it’s Important for Your Blog

 Online Job2 years ago
Online Job2 years ago30 Legitimate Work from Home Jobs with No Startup Fee in 2023

 Online Business Tips3 years ago
Online Business Tips3 years ago35 Best Startup and Small Business Ideas in 2022

 Entertainment2 years ago
Entertainment2 years agoGet to Know Yeh Rishta Kya Kehlata Hai Star Shivangi Joshi’s Net Worth

 Tech2 years ago
Tech2 years agoHow to Play Roblox on School Chromebook When Blocked 2023

 Blog2 years ago
Blog2 years ago10 Best Places to Design and Sell T-Shirts Online and Make Money